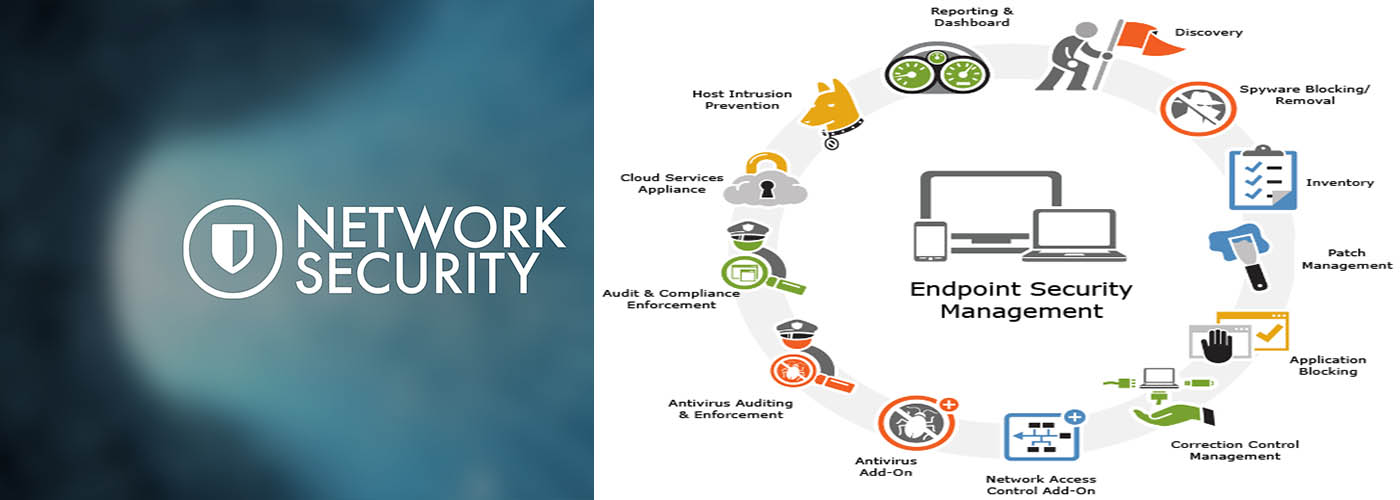
Endpoint security or endpoint protection is an approach to the protection of computer networks that are remotely bridged to client devices. The connection of laptops, tablets, mobile phones and other wireless devices to corporate networks creates attack paths for security threats.
We deploy and maintain simple end point security for your business; which delivers –
- Protect all your devices
- One simplified management console
- On-premises or in the cloud
We also do Endpoint security management – policy-based approach to network security that requires endpoint devices to comply with specific criteria before they are granted access to network resources.